Protect your phone from theft. Protecting your iPhone and Android phone from theft
No hackers or thieves will be scary if you follow our advice. We'll tell you in our article how to secure your gadgets and save information even if your smartphone is lost or stolen.
1 Reduce screen lock time
Simple measure, which will ensure the security of your gadget - a banal screen lock. Configure this function so that the time before turning off the smartphone is minimal. However, if your phone is too easy to activate, locking it alone won't protect it.
The unlock code should be as secure as possible: do not use a pattern, but come up with a PIN code. It is desirable that it contains not 4, but 6 digits. If your smartphone has a fingerprint scanner or facial recognition, don't ignore these features.
2 Activate the search function

Function search will find your smartphone if it is lost or stolen. Search will help not only, but also remotely block or erase data. This way, no attacker will have access to your information.
3 Back up your data

Backing up your data should become a good habit. On the one hand, a backup will help if you lose your smartphone. On the other hand, this will be useful if you remotely deleted data from your smartphone and then found it again. In addition, copied files can be easily transferred to a new device.
4 Install an antivirus program

Viruses can attack not only computers, but also smartphones. There are many antivirus scanners For . For example, AVG Antivirus or Avira Antivir. operating room iOS system not as susceptible to viruses, but not 100% safe.
5 Update your system regularly

Important role System updates play a role in the security of any gadget. If such an update is available, don't hesitate to install it or not, just do it. Updates not only add new features, but also fix bugs previous versions. Sometimes updates also include improvements to systems that protect your smartphone.
6 Encrypt your data

If your phone falls into the wrong hands, attackers will not be able to immediately access your data if it is encrypted. IN Android settings there is a special option that helps encrypt files and prevent unauthorized access. On iPhone, you can encrypt backups or notes with using Touch ID.
7 Download apps only from trusted sources

Do not download applications from dubious sites: use only official sites such as the App-Store or Google Play. However, you shouldn’t download everything here either. Pay attention to how many downloads and ratings an app has and read the list of required permissions. If an app requires too much, stay away from it.
It often becomes a weapon directed against its owner.
As a rule, after stealing a smartphone, the thief studies the information contained on it, trying to find some confidential data, and then changes the SIM card or simply turns off the device.
It would seem that everything, once the device is lost or stolen, it is no longer possible to find or return it to its rightful owner.
But that's not true. If your smartphone has special program, you can track any actions performed on the device and even determine its exact location. And also lock it, so that a thief or someone who accidentally finds it will not be able to read or copy any data. There are many applications designed to block and locate stolen devices, but we will take a look at the five best of them.
Bitdefender Anti-Theft
Bitdefender Anti-Theft is a simple and yet quite effective Anti-Theft for devices running . Application supported quick search devices using an audio signal, determining location through geolocation systems, sending data about a new number to a specified postal address when changing a SIM card, remote deletion of information, as well as complete blocking of the device.
Cerberus
One of the most powerful and effective programs to detect and control a smartphone or Android tablet. Application features include device tracking on a map, blocking secret code, reliable auto-protection, complete erasing of the SD card and the phone’s own memory, monitoring of calls made, providing detailed information about the network and operator, hidden recording sound from the microphone and much more.
Thanks to SMS control, the program performs its functions even if the smartphone is not connected to the Internet. In addition, the SIM-Checker function allows you to find out new number phone if the SIM card is replaced.
Lookout

Lookout is a comprehensive application that combines antivirus and anti-theft. In addition to finding and removing malicious software Lookout also supports finding a device on the map, taking pictures with the built-in camera, sending to a specified email box messages about calls, SIM card changes and other manipulations with the device. Available additional options backup data.
Prey

A powerful application to protect your Android device from theft. Unlike most similar programs, Prey is distributed completely free of charge.
Anti-theft supports searching for devices using geolocation systems, taking pictures with the front and main cameras, completely blocking the device, collecting information about calls and connections, calling using a loud signal, sending messages about changing the SIM card, erasing confidential information.
WatchDroid

A small simple application for basic protection mobile device from theft. WatchDroid can determine the location of a smartphone on a map, delete data, block access, and remotely control certain functions.
Among other features of WatchDroid, it is worth noting that it remembers the last position of the device on the map when the battery is low, and good auto-protection against deletion. Another feature of the application is low energy consumption.
As the developers themselves say, working in background, the application has virtually no effect on the battery drain rate.
A mobile phone is one of the most popular targets for theft. This device is easy to take away, and any reseller will immediately buy it at half price. But technologies are gradually emerging that make such actions meaningless. And today we will talk about 5 Innovative Ways to Protect Your Smartphone.
Remote phone lock
This practice has already been successfully tested by Apple in its laptops. Its essence lies in the ability to remotely block all functions of the device if it is lost or stolen.
Currently, phone owners can download such a program from app stores, but this blocking can be easily bypassed by resetting the smartphone or reflashing it. But the kill switch function, which was originally built-in, involves the complete destruction of the device’s hardware, all personal data and files according to a unique IMEI number. And this will prevent important information from falling into the hands of strangers, and will generally make it impossible to work with a stolen device.

Government South Korea, concerned about the one and a half times increase in the number of mobile phone thefts over the year, is going to oblige manufacturers to equip all phones with a kill switch function. Samsung was the first to decide on this innovation - its new product Samsung Galaxy S5 is equipped with the ability to find a smartphone and lock it remotely.
Fingerprints
For a century, fingerprints have been used primarily in forensic science. But within a few years, portable scanners may appear in the pockets of most people around the world. After all, mobile phone manufacturers began to use skin patterns on the fingers that are unique to each person to identify the smartphone user.
When turning on the phone, the owner only needs to place his finger on the scanner to unlock his smartphone. At the same time, the user’s relatives or friends can take advantage of the same right if their fingerprints are also included in the device’s database. But strangers will not be able to turn on the smartphone under any circumstances.

Nowadays, manufacturers equip their top models of mobile phones with a fingerprint scanner, for example, this function is available in the iPhone 5S, HTC One Max, Samsung Galaxy S5, Motorola ES400 and some other devices.
Phone alarm
Another popular way to protect your phone from theft is to install on it beep ization. Unlike the features mentioned above, this one is available not only for top models, but for any smartphone. After all, the program can be downloaded from the application store, and it will work even on the cheapest device.
Various developers offer different options. Some applications trigger a sound when the smartphone is disconnected from the charger. There are programs that are activated every time you touch an unattended phone. And there are developments that allow you to turn on the alarm remotely - via SMS with a special set of characters or via the Internet.
Phone self-destruction
This technology has been developed, but has not yet been implemented in the production of mobile phones. It is based on a special polymer board, which can melt when receiving an external signal, after which the device cannot be used.The first mobile phone equipped with such a board was presented in early April at an exhibition in Dallas by scientists from Iowa State University. In front of many spectators, the insides of the device were melted after sending an SMS to it.

According to the creators of this technology, it can be used in the production of mobile phones and bank cards– two items, the loss or theft of which could lead to significant trouble for the former owner.
Charger password
Two years ago Apple Corporation has patented perhaps the most radical system for protecting laptops and mobile phones from theft. The developers propose to store additional password to the device in a special memory module built into the charger.After all, the password on the phone can be bypassed by changing the firmware. But such fraud will become meaningless if the smartphone loses its original charger, which is one of the parts of the mobile phone authentication.

An attacker will not be able to start a mobile phone after its battery is discharged; the device will refuse to accept someone else’s charge. At the same time, the owner of the phone himself can easily use someone else’s charger, knowing an additional password recognized by the smartphone.
In this case, such applications come to the rescue to locate, block, obtain information about the use of programs, obtain photos remotely and provide evidence for a possible police investigation.
We have prepared this list of five free applications determine the location of the smartphone and each contains links to obtain additional information and possible download from Google Play.
1. Lost Android:
This is a very valuable application in case of theft or loss mobile phone, which allows you to accurately determine your location through the AndroidLost.com network. We recommend first!
Some of his most interesting features are:
Send a pop-up message to your device so the finder can contact you
-Lock your device with a password
-View calls and messages sent and received
-Send location message using another mobile phone
2. Prey Anti-Theft:
Prey is small program, which will help you find your phone, laptop or tablet if it ever disappears. Works on Mac, Windows, Linux, Android and also comes with open source code 100% free.
Once the emergency protocol is activated, you receive reports every twenty minutes from the missing device.


Once you log into Prey you can do the following:
— Find your phone on the map via geolocation using GPS and WiFi triangulation
- Take a photo using the built-in front and rear camera
— Block device
— Trigger a loud alarm remotely, even if the phone is on silent
— Display a warning message on the screen
-Get network information as soon as the device connects (for precise definition location)
- Detect change in active SIM card
— Protect the application from deletion
— Activate the application with via SMS from any phone and get a report instantly
3. Find My Phone:
There is another application for mobile search. Find My Phone takes advantage of modern GPS technologies to pinpoint the phone's location.
Note: For this feature to work, Find app My Phone must be installed on the phone and on the phone of the person you want to track or find, so add Find My Phone app on cell phones for all members of your family.

Where is the phone?
Maybe you've heard of "triangulation" in TV shows like CSI. And this is how the app on the phone actually works. Mobile companies know the mobile location because they know the distance from the phone to cell tower. Find My Phone receives this data from operators cellular communication and displays its location on the map.
4. Where's My Droid:
Wheres My Droid was created as a simple app so that when you lose your phone in your home, you can signal to find it, but every month the developer adds new features.

How this app works:
For example, you have a device in silent mode and you don't know where you left it. You just find another computer and send text message With keyword, which you have chosen in advance, you have chosen and just wait, it will automatically activate the sound and begin to report where it is.
The application can also receive GPS coordinates phone number with a link to Google maps, if you are not close enough to your phone and do not hear the ringing.
Features of application:
~ Find your phone by turning on sound/vibration
~ Find your phone using GPS locations
~ Sending test commands
~ Password protection to prevent unauthorized changes to the application
~ Notification of changed SIM card or phone number
~ Stealth Mode hides incoming text with command words
~ White/Blacklist allows you to control who cannot use the application via text commands
~ Does not affect battery charge
Additional features in Pro versions:
~ Take pictures from your device's camera
~ Remotely lock your device
~ Remotely erase memory card
~Remotely erase phone data
~Use landlines to activate the application
~ Set up a ringtone if lost (Pro or with registration)
Standard application from Google. Are you afraid of losing your phone? Thanks to Remote Android control you can be calm about your device and the data on it. This feature allows you to:
- determine the location of the Android device associated with your Google account
- reset screen lock PIN
- delete all data from the device
- beep on the device
To clarify the location of your mobile phone, you must have access to account, created on the Google website.

Briefly: If you use a graphic key to access your phone, then 99% of the time this is enough to ensure that no one can access the information on your phone without your knowledge. If the data on your phone is very sensitive, then you should use the built-in function full encryption phone.
Today, almost all smartphones have become carriers of important personal or corporate data. Also, through the owner's phone, you can easily access his accounts, such as Gmail, DropBox, FaceBook and even corporate services. Therefore, to one degree or another, it is worth worrying about the confidentiality of this data and using special means to protect your phone from unauthorized access in case of theft or loss.
- From whom should you protect your phone data?
- Built-in data protection in Android.
- Full phone memory encryption
- Results
What information is stored on the phone and why protect it?
A smartphone or tablet often serves as a mobile secretary, freeing the owner’s head from storage large quantity important information. The phone book contains numbers of friends, co-workers, and family members. IN notebook they often write numbers credit cards, access codes to them, passwords to social networks, email and payment systems.
The list of recent calls is also very important.
Losing your phone can be a real disaster. Sometimes they are stolen specifically to penetrate personal life or to share profits with the owner.
Sometimes they are not stolen at all, but are used for a short time, unnoticed, but a few minutes is quite enough for an experienced malicious user to find out all the details.
The loss of confidential information can result in financial ruin, ruin personal life, family breakdown.
I wish I didn't have it! - the former owner will say. - It’s so good that you had him! - the attacker will say.
And so what needs to be protected on the phone:
- Accounts. This includes, for example, access to your email gmail mailbox. If you have set up synchronization with facebook, dropbox, twitter. Logins and passwords for these systems are stored in clear text in the phone profile folder /data/system/accounts.db.
- History of SMS correspondence and phone book also contain confidential information.
- Web browser program. The entire browser profile must be protected. It is known that Web Browser(built-in or third-party) remembers all passwords and logins for you. This is all stored in open form in the program profile folder in the phone’s memory. Moreover, usually the sites themselves (using cookies) remember you and leave access to your account open, even if you did not specify to remember the password.
If you are using sync mobile browser(Chrome, FireFox, Maxthon, etc.) with a desktop version of the browser to transfer bookmarks and passwords between devices, then you can assume that you can access all passwords from other sites from your phone. - Memory Card. If you store confidential files on the memory card or download documents from the Internet. Typically, photos and videos taken are stored on a memory card.
- Photo album.
Who should you protect your phone data from:
- From a random person who finds your lost phonel because from “accidental” theft of the phone.
It is unlikely that the data on the phone will be of value to the new owner in this case. Therefore, even simple graphic key protection will ensure data safety. Most likely, the phone will simply be reformatted for reuse. - From prying eyes(co-workers/children/wives), who can gain access to your phone without your knowledge, taking advantage of your absence. Simple protection will ensure data safety.
- Providing forced access
It happens that you are voluntarily forced to provide a phone number and open access to the system (information). For example, when your wife, government official or employee asks you to look at your phone service center Where did you take your phone for repair? In this case, any defense is useless. Although it is possible using additional programs, hide the fact of the presence of some information: hide part of the SMS correspondence, part of the contacts, some files. - From targeted theft of your phone.
For example, someone really wanted to know what was on your phone and made an effort to get it.
In this case, only full encryption of the phone and SD card helps.
Built-in data protection on Android devices .
1. Lock screen with Pattern Key.
This method is very effective in the first and second cases (protection against accidental loss of the phone and protection from prying eyes). If you accidentally lose your phone or forget it at work, no one will be able to use it. But if your phone purposefully fell into the wrong hands, then this is unlikely to save you. Hacking can even occur at the hardware level.
The screen can be locked with a password, PIN code and Pattern Key. You can select the locking method by launching the settings and selecting the Security -> Screen lock section.
Graphic Key(Pattern) - c the most convenient and at the same time reliable way phone protection.

None- lack of protection,
Slide— to unlock, you need to swipe your finger across the screen in a certain direction.
Pattern- this is a Graphic Key, it looks something like this:
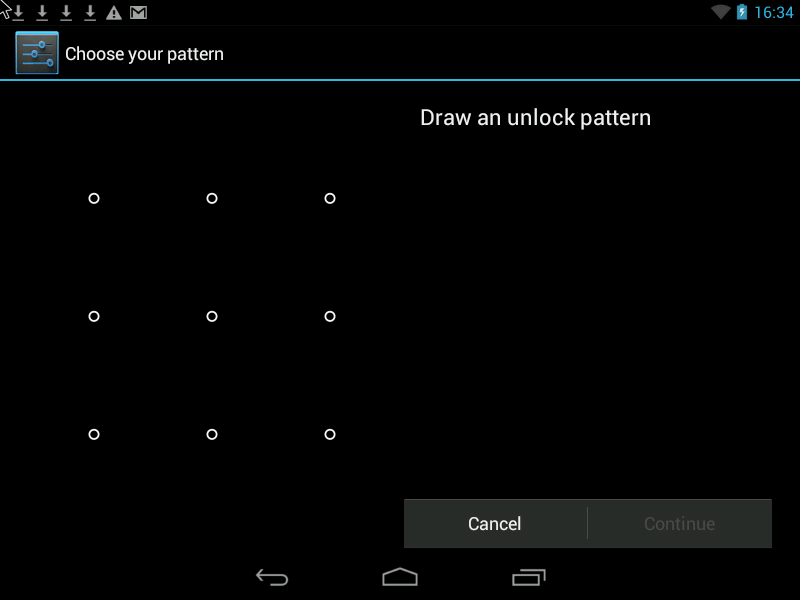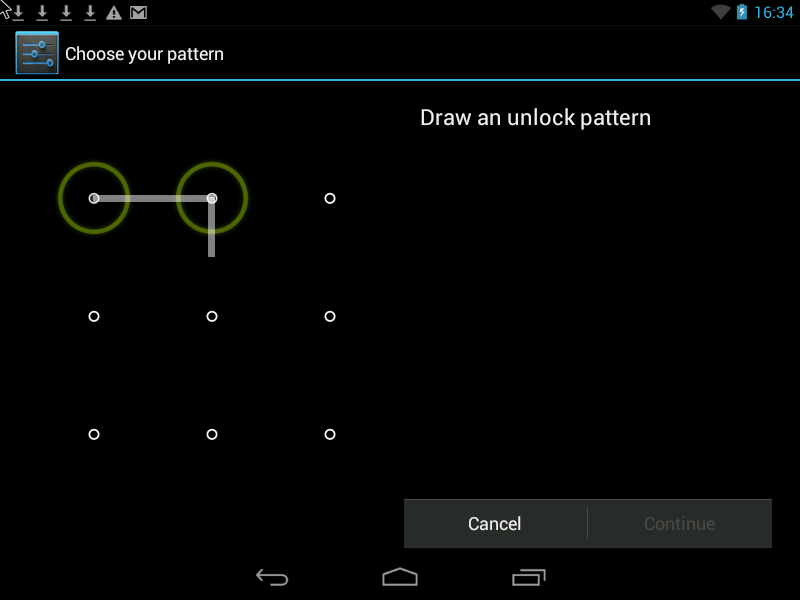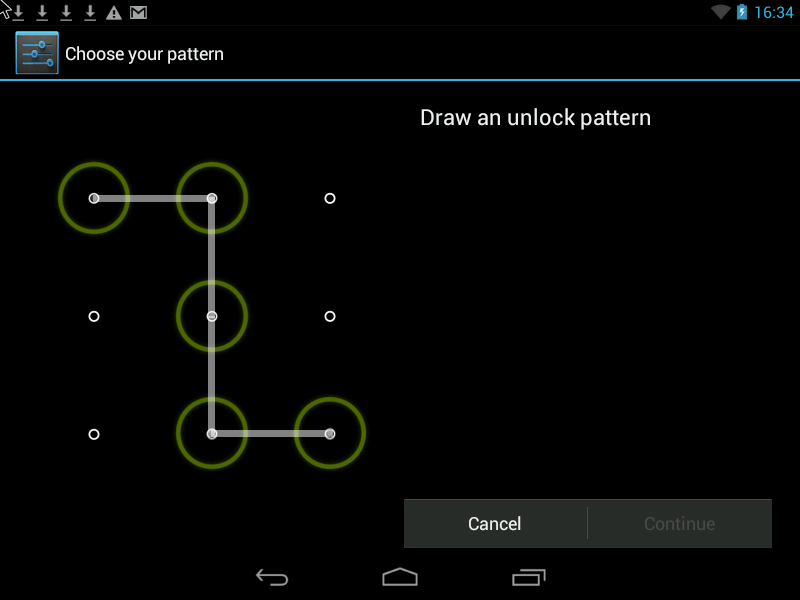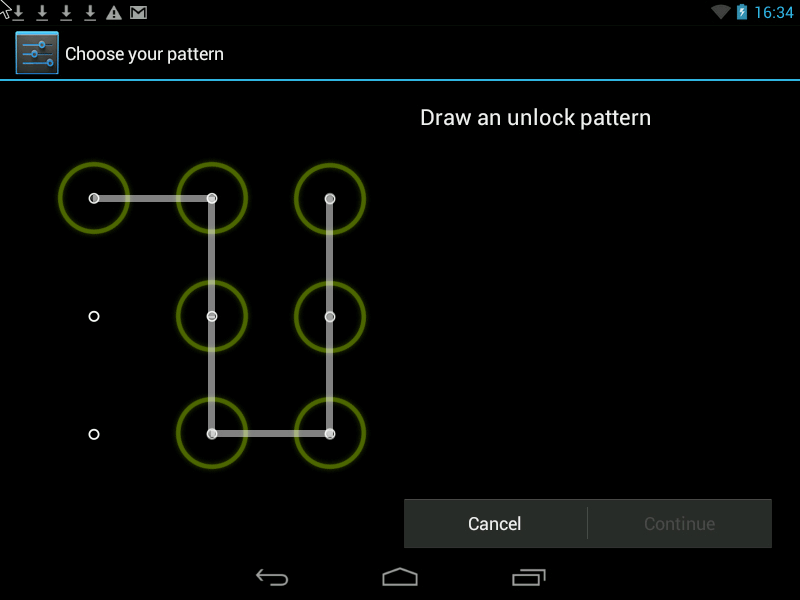
You can improve security in two ways.
1. Enlarge the Graphic key input field. It can vary from 3x3 dots on the screen to 6x6 (Android 4.2 is found in some models, depending on the Android version and phone model).
2. Hide the display of the points and “path” of the graphic key on the smartphone screen so that it is impossible to peek at the key.
3. Install automatic blocking screen after 1 minute of phone inactivity.
Attention!!! What happens if you forgot your pattern key:
- The number of incorrect attempts to draw a Graphic Key is limited to 5 times (per various models number of attempts can be up to 10 times).
- After you have tried all your attempts but still have not drawn the Pattern Key correctly, the phone is locked for 30 seconds. After this, you will most likely have a couple of attempts again, depending on your phone model and Android version.
- Next, the phone asks for the login and password of your Gmail account, which is registered in the phone’s Accounts settings.
This method will only work if your phone or tablet is connected to the Internet. Otherwise deadlock or reboot to manufacturer settings.
It happens that the phone falls into the hands of a child - he starts playing, draws the key many times and this leads to the key being blocked.
PIN is a password consisting of several numbers.
And finally, Password— the most reliable protection, with the ability to use letters and numbers. If you decide to use a password, then you can enable the Phone encryption option.
Encryption of phone memory.
Feature included in the package Android versions 4.0* and higher. for tablets. But this feature may be missing in many budget phones.
Allows you to encrypt your phone's internal memory so that it can only be accessed using a password or PIN code. Encryption helps protect the information on your phone in the event ts
targeted theft. There is no way that attackers will be able to access your data from your phone.
A prerequisite for using encryption is to set a screen lock using a password.
This method achieves saving user data located in the phone memory, for example phone book, browser settings, passwords used on the Internet, photos and videos that the user received using the camera and did not transfer to the SD card.



— SD card encryption is enabled as a separate option.
— Memory encryption may take up to an hour depending on the amount of memory on the device. The phone cannot be used during encryption.
What if you forgot your password?
Password recovery is not provided in this case. Can be done on a phone or tablet full RESET, i.e. reinstall Android, but user data from the phone or tablet will be erased. Thus, if an attacker does not know the password to unlock the phone, he will not be able to use it. It will also be impossible to see data from the phone’s memory using other programs by connecting the phone to a computer, because all internal memory is encrypted. The only way to get your phone working again is to reformat it.
Attention, the full encryption function is present only starting from Android OS 4.0 - 4.1 and may simply not be available on some phone models. Most often found in phones from Samsung, HTC, LG, Sony. Some Chinese models also have an encryption function. On some phones, this function is located in the “Memory” section.
Flaws:
- You will need to constantly enter quite complex password(6-10 characters) even if you just want to call. Although it is possible to set a long time interval (30 minutes) during which the password will not be requested when you turn on the phone screen. On some phone models, the minimum password length can be from 3 characters.
- On some phone models, it is not possible to disable encryption if you want to avoid having to constantly enter a password. Encryption can only be disabled by returning the phone to factory settings and erasing all data.
Encrypting an external SD memory card
Feature included as standard Android package 4.1.1 for tablets. Missing from many budget builds.
The function provides reliable protection data on external SD card. Personal photos can be stored here, text files with commercial and personal information.
Allows you to encrypt files on the SD card without changing their names, file structure, with saving preview graphic files (icons). The function requires setting a display lock password of at least 6 characters.




It is possible to cancel encryption. When changing the password, automatic re-encryption occurs.
If the user has lost the memory card, encrypted files cannot be read through the card-reader. If you put it on another tablet with a different password, then the encrypted data also cannot be read.
Other Encryption Properties:
- Transparent encryption. If the card is inserted into the tablet and the user has unlocked the screen with a password, any application sees the files in decrypted form.
- If you connect the tablet via a USB cable to a computer, encrypted files can also be read on the computer by first unlocking the card from the screen of the mobile device.
- If you write some other unencrypted files onto the card via the card-reader, they will also be encrypted after inserting the card into the tablet.
- If you have an encrypted card, you cannot cancel the lock password.
- Data is encrypted at the file level (the file names are visible, but the contents of the file are encrypted).
Disadvantage of the program:O missing from most Android builds.
It should be emphasized that the best safety of data is a complete copy of it on your Computer in A smartphone is a fairly fragile small device, which means there is always a possibility of it breaking or being lost.
Improving the usability of a secure smartphone
Full phone encryption provides the strongest level of protection, but constantly entering a 6-digit password makes it difficult to use. But there is a solution.
IN Android system from version 4.2* it is possible to move some applications\widgets to the lock screen, and thus you can perform simple steps without constantly unlocking the phone (without entering a 6-digit password).
Results:
- Built-in and free features to protect the phone are very reliable. They are able to protect against prying eyes user contacts, correspondence and calls, accounts in various programs and networks, as well as files and folders located both in the phone memory and on a removable SD card.
- Before buying a phone, you should make sure how the required protection works in this particular phone model: the requirement to use an overly complex PIN code or password on the lock screen (Pattern Key is not suitable), irreversible encryption internal memory phone, i.e. The only way to opt out of encryption is full reset phone settings.
- Important! Make sure that if you forget your password or Graphic Key, you can restore access to your phone or you can easily restore your phone settings and information if you have to hard reset(resetting the phone to factory settings with loss of all data).
- Keep backup copy confidential data is required only on your Computer, on DVD disc or in the cloud.